“John Doe” Instances
When reviewing your AWS EC2 usage, you may find instances or volumes without a name, or even worse, with a name that isn’t clear. These resources might be a complete waste of money or critical to production workloads.
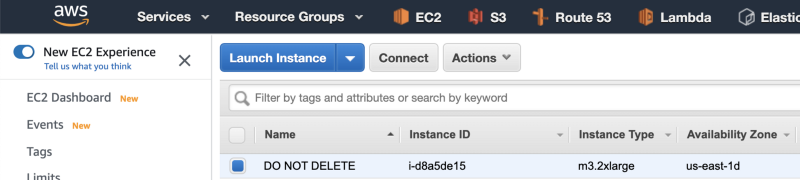
The instances could be several years old, with no one in the organization having information about the instances or the credentials to connect to the instances.
To avoid this problem, companies enforce tagging policies, where every instance you provision must have†m a Name/Owner/Project/etc. tag.
There is no additional cost for tagging EC2 Instances and Volumes…
…however, since people are launching instances and writing automation scripts that launch instances, this process can be error-prone.
To avoid these cases, I wrote a solution for AWS (and a similar one for Google Cloud) that automatically tags the instances with the Owner tag and the volumes with Owner and AttachedInstance tags.
So in the future, if someone encounters an instance or a volume whose purpose is unknown, these tags will make it easier to identify who set it up.
How does auto-tagging work?
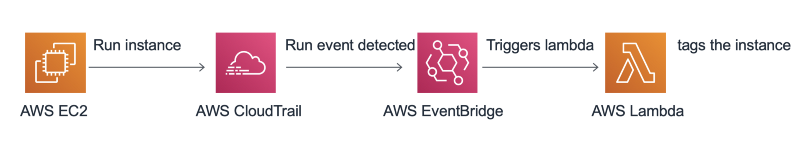
- User creates an AWS EC2 instance.
- AWS CloudTrail tracks the API calls and calls AWS EventBridge.
- AWS EventBridge triggers the Lambda function.
- AWS Lambda tags the instance and the instance volumes.
Once the AWS Lambda function is triggered with the instance launch information, it will tag the instance with the Owner tag, and the tag will contain one of the following:
- IAM User
- Assume Role (For example AutoScaling Role, SSO user and etc).
- Root User
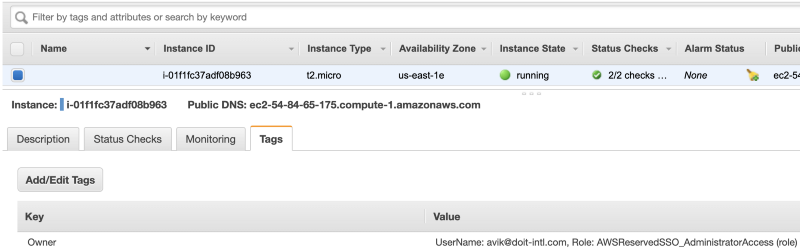
In the next stage, Lambda will tag all the instance volumes with the ‘Owner’ and ‘AttachedInstance’ tags. The ‘Owner’ tag will contain the same information as the instance ‘Owner’ tag, and the ‘AttachedInstance’ tag will contain the instance-id and instance name if the instance name exists.
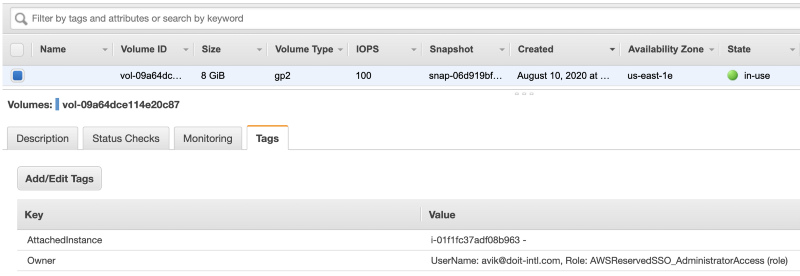
How to implement:
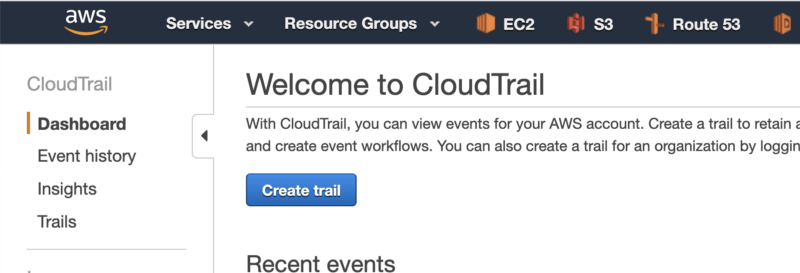
- Go to the CloudTrail page and click on “Create trail”.
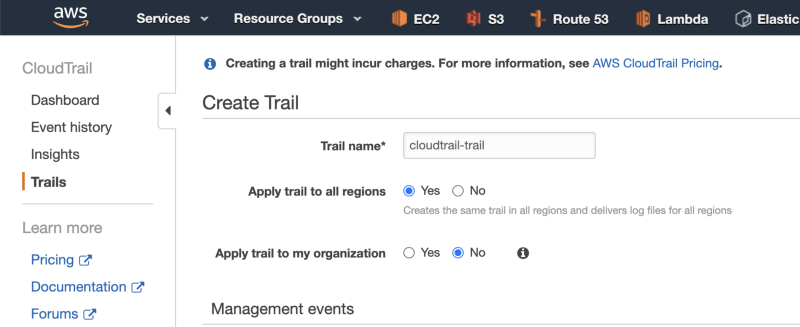
2. Give the trail a name.
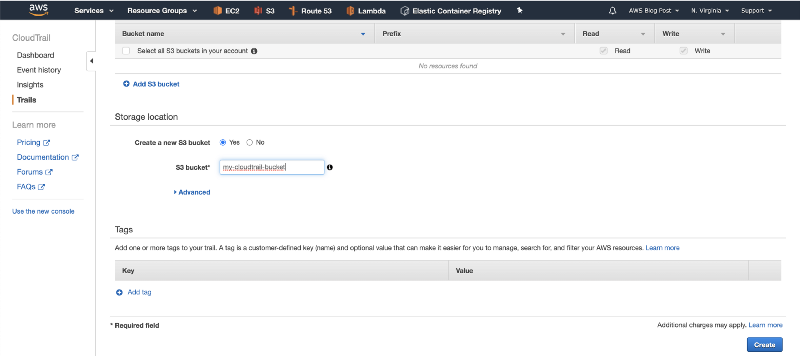
3. Scroll down and set a name for the CloudTrail S3 bucket. Then click on Create.
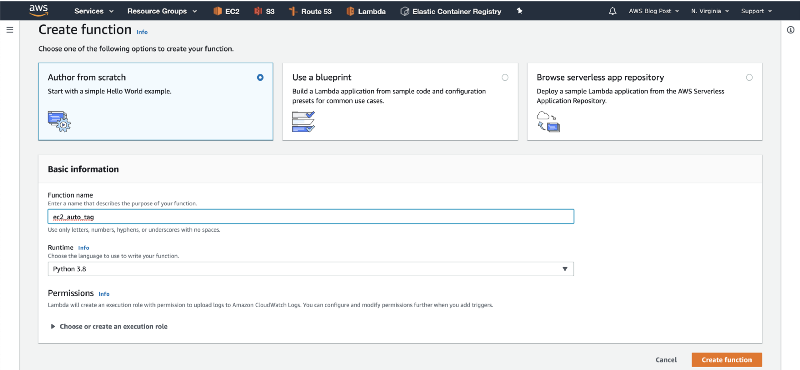
4. Navigate to the Lambda dashboard, and click on “Create function”.
5. Give the function a name, select “Python 3.8” in the Runtime dropdown, and click on “Create Function”.
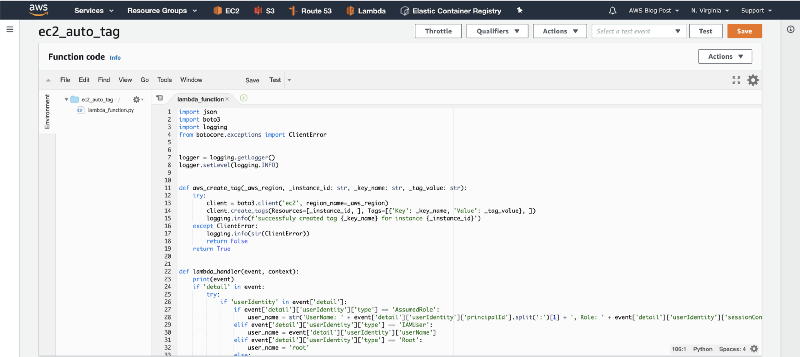
6. Paste the code from the Github repository, and click on “Save”.
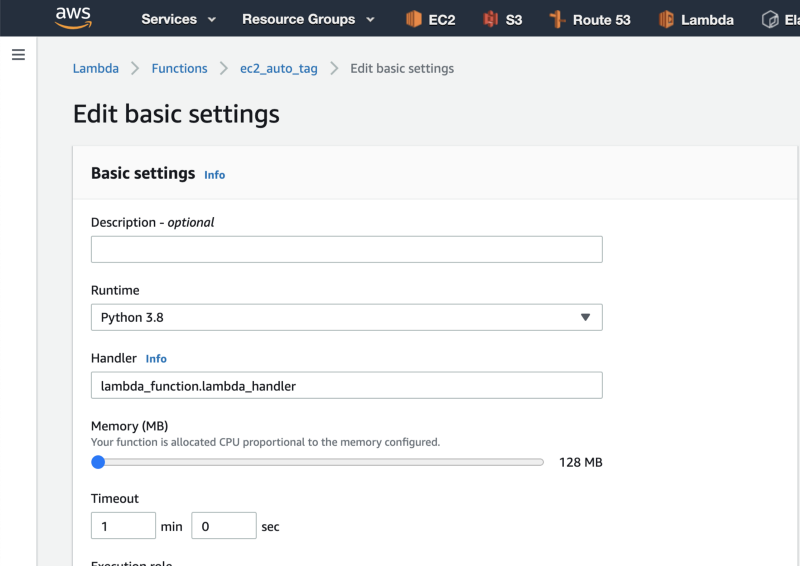
7. Scroll down to the “Basic settings” box, and click on the Edit button.
Then increase the Lambda function’s timeout to 1 minute.
Next, click on the Save button.
8. Scroll back up and click on Permissions. Then click on the Role name.
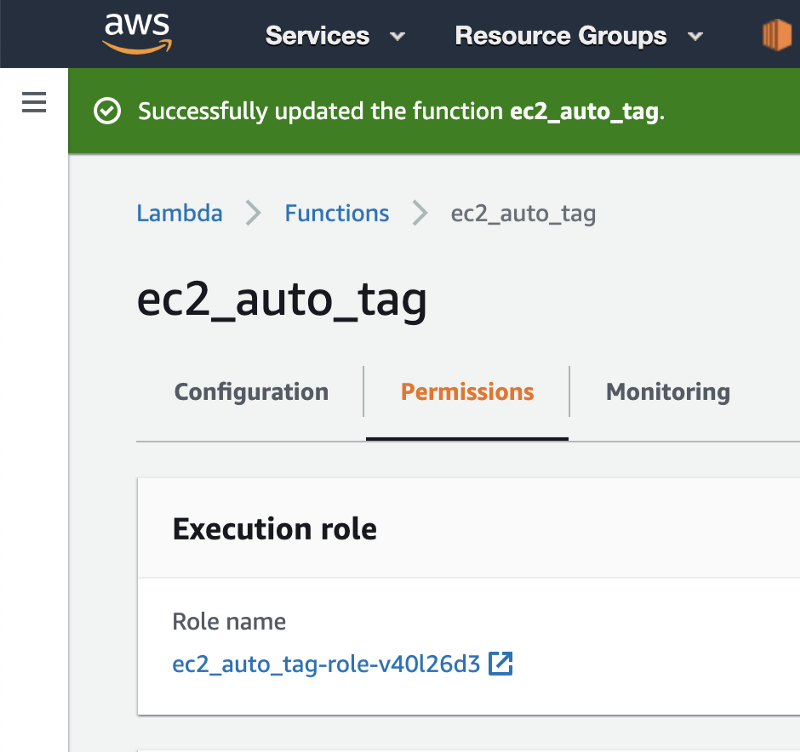
9. Click on the “Add inline policy” button.
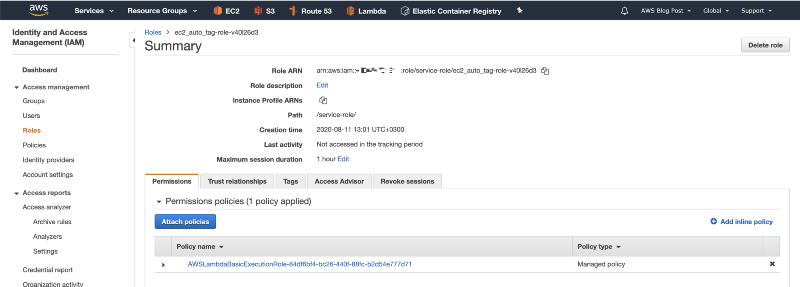
10. Click on the JSON button, paste the following IAM policy, and click on Review policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "ec2:CreateTags",
"Resource": [
"arn:aws:ec2:*:*:instance/*",
"arn:aws:ec2:*:*:volume/*"
]
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"ec2:DescribeInstances",
"ec2:DescribeVolumes"
],
"Resource": "*"
}
]
}
This policy will allow the Lambda function to discover the instance volumes, and to tag the instance and the instance volumes.
11. Give the policy a name and click on Create policy.
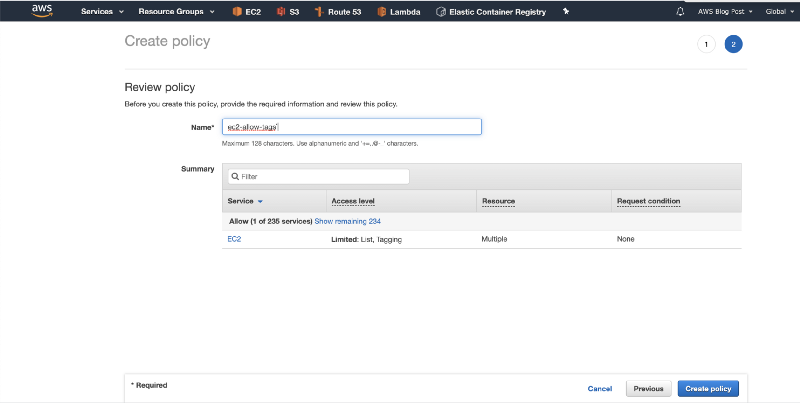
12. Go back to the Lambda tab in your browser, and click on “Add trigger”.
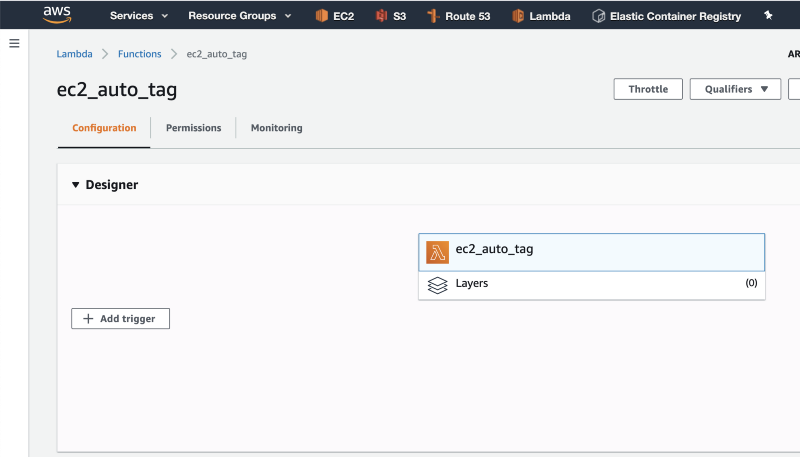
13. Click on “Select a trigger”, search for EventBridge, and then click on “Create a new rule” in the Rule dropdown.
Give your rule a name and description.
Under “Rule type”, select the Event pattern radio button.
In the first dropdown, choose EC2, and in the second dropdown, select AWS API call via CloudTrail.
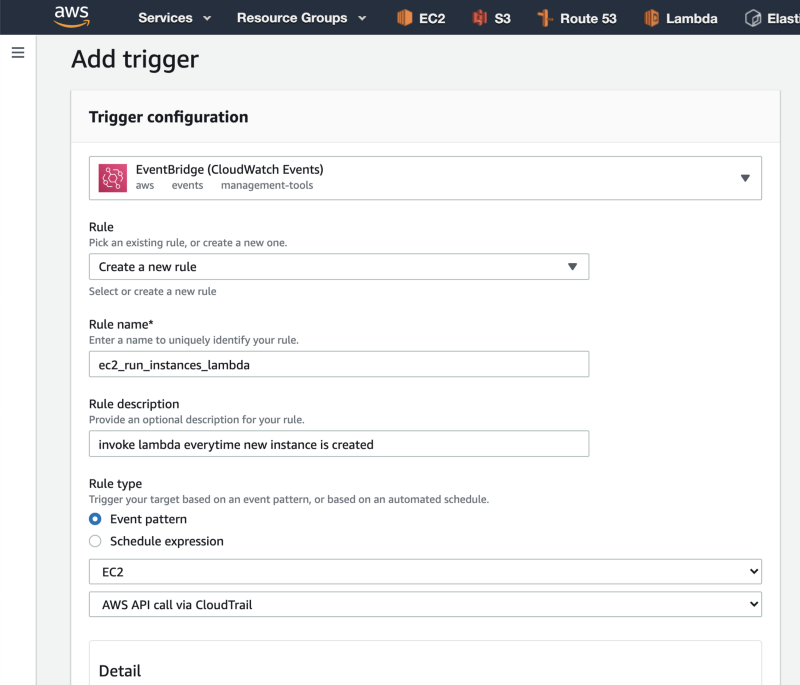
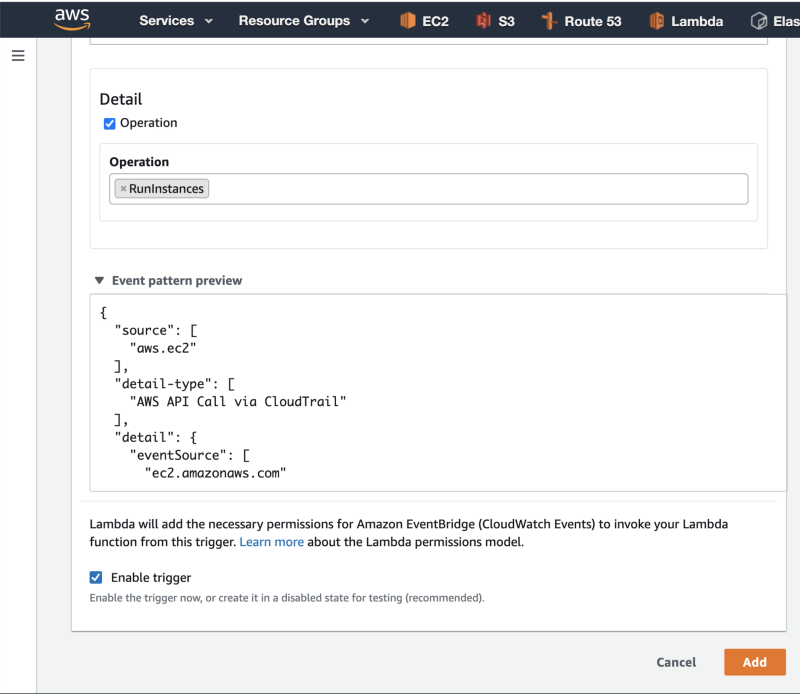
14. Scroll down, click on the Operation checkbox, and under Operation, type RunInstances. then click on the Add button to create the event trigger.
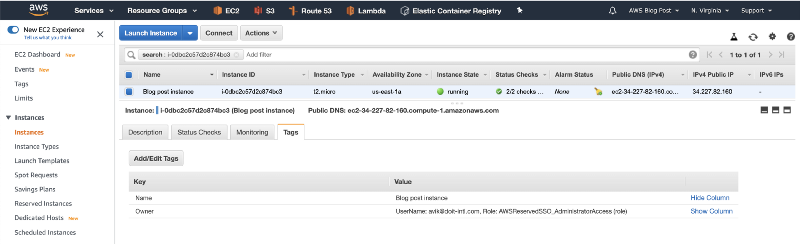
15. Finally, deploy a new test instance to check that everything works.
After a few seconds, the Lambda function we implemented will automatically tag the instance and volume(s).
Refresh the page and check the instance tags.
Notes:
- This solution will tag only newly created instances after you installed the Lambda function.
- If you just turned on the CloudTrail trail, it might take up to an hour until EventBridge will start invoking the function.
- CloudTrail’s response size is limited to 500Kb. If you launch a large number of instances with one API call, the Lambda function will not be able to tag the instances.
- AWS EventBridge is a regional resource. If you are working with multiple regions, you will need to deploy the solution in every AWS region.