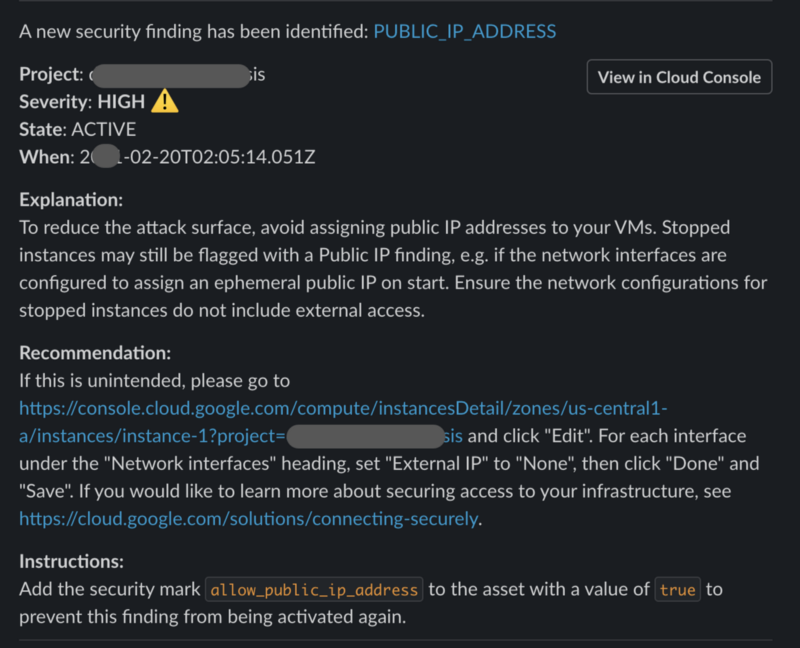
Never miss out on SCC Findings again.
Google Security Command Center (SCC) surfaces security issues in the form of Findings. In a previous article, we explored how to extend SCC’s notifications to make security Findings more visible, and available in Cloud Monitoring for metrics and alerting.
In this post, you’ll learn another option to extend the visibility of those Findings even further by sending them a Slack channel automatically.
The project is a Google Cloud Function that is triggered by SCC Findings sent to a PubSub Topic. The PubSub configuration may be set up using the related project https://github.com/gschaeffer/scc-alerts. The default filter is for high severity Findings.
Requirements
SCC Notifications must be set up. That process is simplified using the related project https://github.com/gschaeffer/scc-alerts.
Installation
Set the project value for the gcloud commands.
PROJECT="[REPLACE_WITH_PROJECT_ID]" gcloud config set core/project $PROJECT # Verify the change gcloud config get-value core/project
Create secrets in Cloud Secret Manager. Enable the service if it is not already enabled.
# Create secret 'slack-token'; replace value including brackets. print | gcloud secrets create slack-handler-token --data-file=- --replication-policy user-managed --locations us-central1 # Create secret 'slack-channel'; replace value including brackets. print | gcloud secrets create slack-handler-channel --data-file=- --replication-policy user-managed --locations us-central1
Deploy the cloud function
# Clone the repo git clone
https://github.com/gschaeffer/scc-slack-handler
# Update the project id sed -i deploy_func.sh # Deploy the Cloud Function ./deploy_func.sh
Cleanup
To remove resources use the gcloud scripts below.
# Remove the Cloud Function gcloud functions delete # Remove the secrets gcloud secrets delete slack-handler-token gcloud secrets delete slack-handler-channel
Originally published at https://github.com.



