In our modern world, data travels between networks and systems without any hindrance. Therefore, it has become vital to implement strong security measures to safeguard sensitive information. Although inbound traffic filtering receives significant attention, the importance of egress filtering should not be underestimated. Egress filtering enables organizations to regulate outbound network communication, ensuring that only authorized and secure connections are established.
One of the leading techniques for egress filtering is Fully Qualified Domain Name (FQDN) filtering. This approach gives administrators precise control over outbound traffic by domain names. When used with Google Cloud Platform's (GCP) Firewall Policy, organizations can enjoy exceptional security and management of their network egress points.
In this blog post, we will walk you through the process of implementing FQDN egress filtering in GCP using FQDN objects in the firewall policy rules.The Firewall policy is a separate feature in the cloud firewall, and it offers a lot of features compared to the VPC firewall rules
The FQDN object in the firewall policy rule feature is currently in preview, and no SLAs or technical support commitments are provided by GCP support.
What is a Firewall Policy?
Google Cloud Platform (GCP) Firewall Policy is a network security feature provided that allows you to define and enforce centralized firewall rules for your virtual machine (VM) instances and VPC (Virtual Private Cloud) networks.
It provides a unified and scalable approach to managing network traffic, allowing you to control inbound and outbound communication, filter traffic based on various criteria, and enhance overall security.
With Firewall Policy, you can define fine-grained rules that specify which types of traffic are allowed or denied based on factors such as IP ranges, ports, protocols, and even Fully Qualified Domain Names (FQDNs). This enables you to establish a secure network perimeter and protect your cloud resources from unauthorized access or malicious activities.
Key features and benefits of the GCP Firewall Policy include the following:
- Centralized Management: You can manage and configure firewall rules across multiple projects, regions, and VPC networks from a single, centralized interface, simplifying the management of network security policies.
- Flexible Rule Definitions: Cloud Firewall Policy allows you to define rules based on IP addresses, ranges, ports, protocols, and FQDNs. This flexibility enables granular control over inbound and outbound traffic, allowing you to define highly specific security policies.
- Dynamic Updates: You can modify firewall rules in real time, allowing you to adapt to changing network security requirements without disrupting existing network traffic.
- Integration with Google Cloud Services: Cloud Firewall Policy seamlessly integrates with other Google Cloud services, such as VPC networks, load balancers, and VM instances, providing consistent security controls across your entire infrastructure.
- Logging and Monitoring: Cloud Firewall Policy provides detailed logging and monitoring capabilities, enabling you to gain visibility into network traffic, analyze security events, and troubleshoot potential issues effectively.
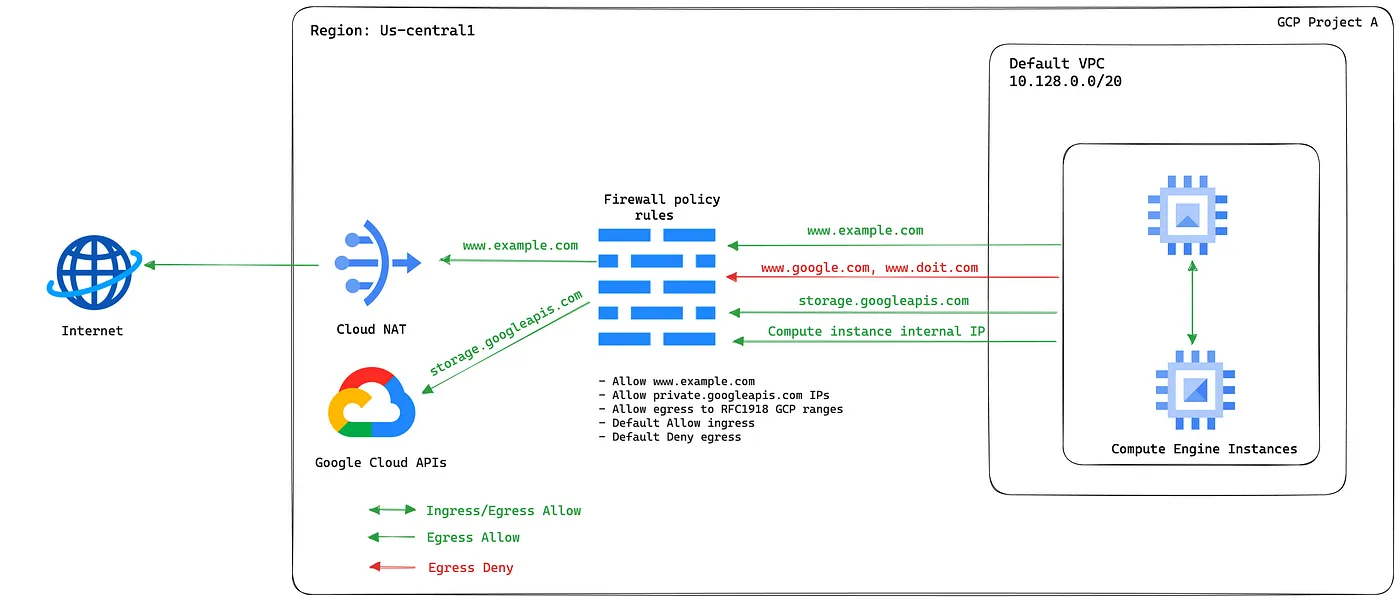
Reference Architecture
Sample setup
Implementation steps for the reference architecture
- Setup Private Google Access
- Cloud NAT for Internet access
- Setup firewall policy rules
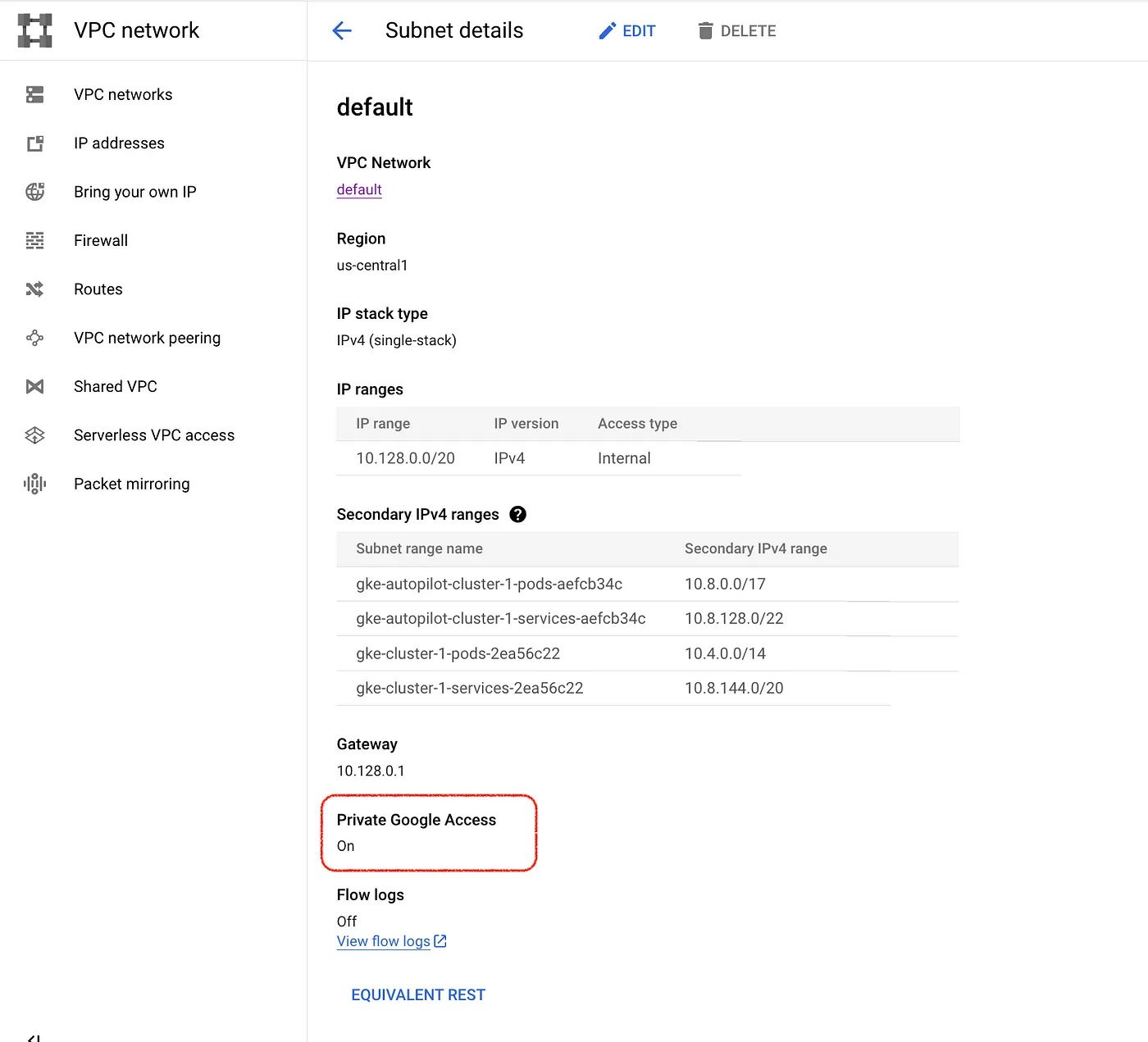
Setup Private Google Access
Private Google Access allows resources within a Virtual Private Cloud (VPC) network to access Google services using private IP addresses without needing external internet connectivity.
We also need to set up Private google access with private.googleapis.com or restricted.googleapis.com domain to ensure requests to Google APIs are only routable within Google Cloud.
Private Google Access is enabled on a per-subnet basis. Enable Private Google Access on an existing subnet and update the variables.
gcloud config set project $PROJECT_ID gcloud compute networks subnets update $SUBNET_NAME \ --region=$REGION \ --enable-private-ip-google-access
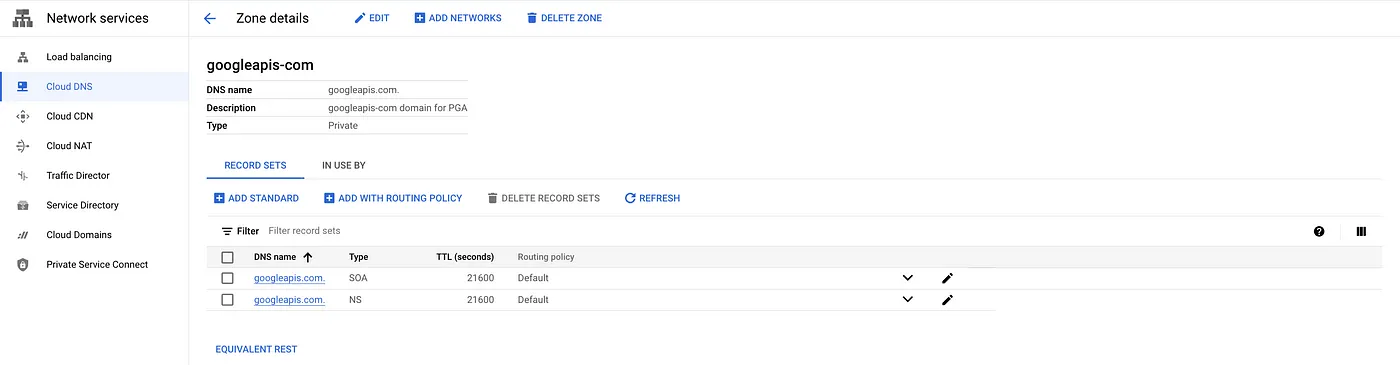
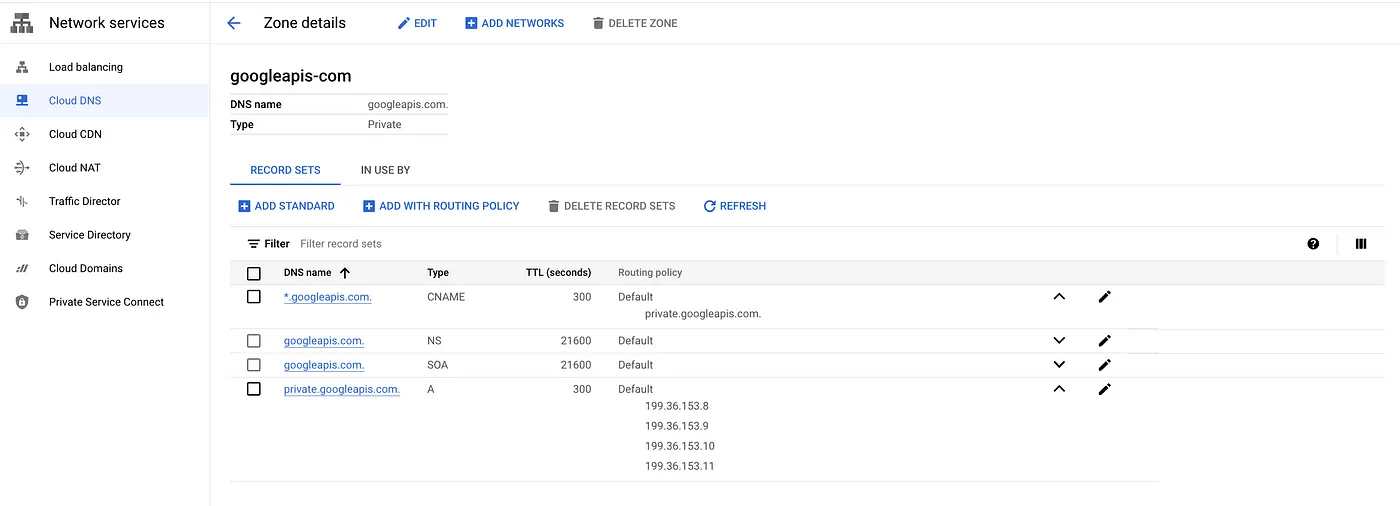
For this setup, we need to create cloud DNS zones for private.googleapis.com. Userestricted.googleapis.com if you are using VPC service control. Refer to Domain options for more details.
Create a private DNS zone for googleapis.com
gcloud dns managed-zones create googleapis-com \ --dns-name=googleapis.com. \ --description="googleapis-com domain for PGA" \ --visibility=private \ --networks=$NETWORK_NAME
Create an A record for private.googleapis.com pointing to the following IP addresses: 199.36.153.8 , 199.36.153.9 , 199.36.153.10 , 199.36.153.11 .
gcloud dns record-sets create "private.googleapis.com." \<br> --type="A" \<br> --ttl="300" \<br> --rrdatas="199.36.153.8,199.36.153.9,199.36.153.10,199.36.153.11" \<br> --zone="googleapis-com"
Create a CNAME record for *.googleapis.com that points to the domain that you've configured: private.googleapis.com .
gcloud dns record-sets create "*.googleapis.com." \ --type="CNAME" \ --ttl="300" \ --rrdatas="private.googleapis.com." \ --zone="googleapis-com"
Some Google APIs and services are provided using additional domain names, including *.gcr.io , *.gstatic.com , *.pkg.dev , and pki.goog.
Refer to the domain and IP address ranges table in Domain options to determine if the additional domain's services can be accessed using private.googleapis.com or restricted.googleapis.com .For example, if you use Google Kubernetes Engine (GKE), you also need to configure *.gcr.io and *.pkg.dev private zones in Cloud DNS.
Setup Cloud NAT
Cloud NAT is a distributed, software-defined managed service that lets resources without external IP addresses create outbound connections to the internet. Cloud NAT is recommended instead of the default internet gateway to control the outbound traffic.
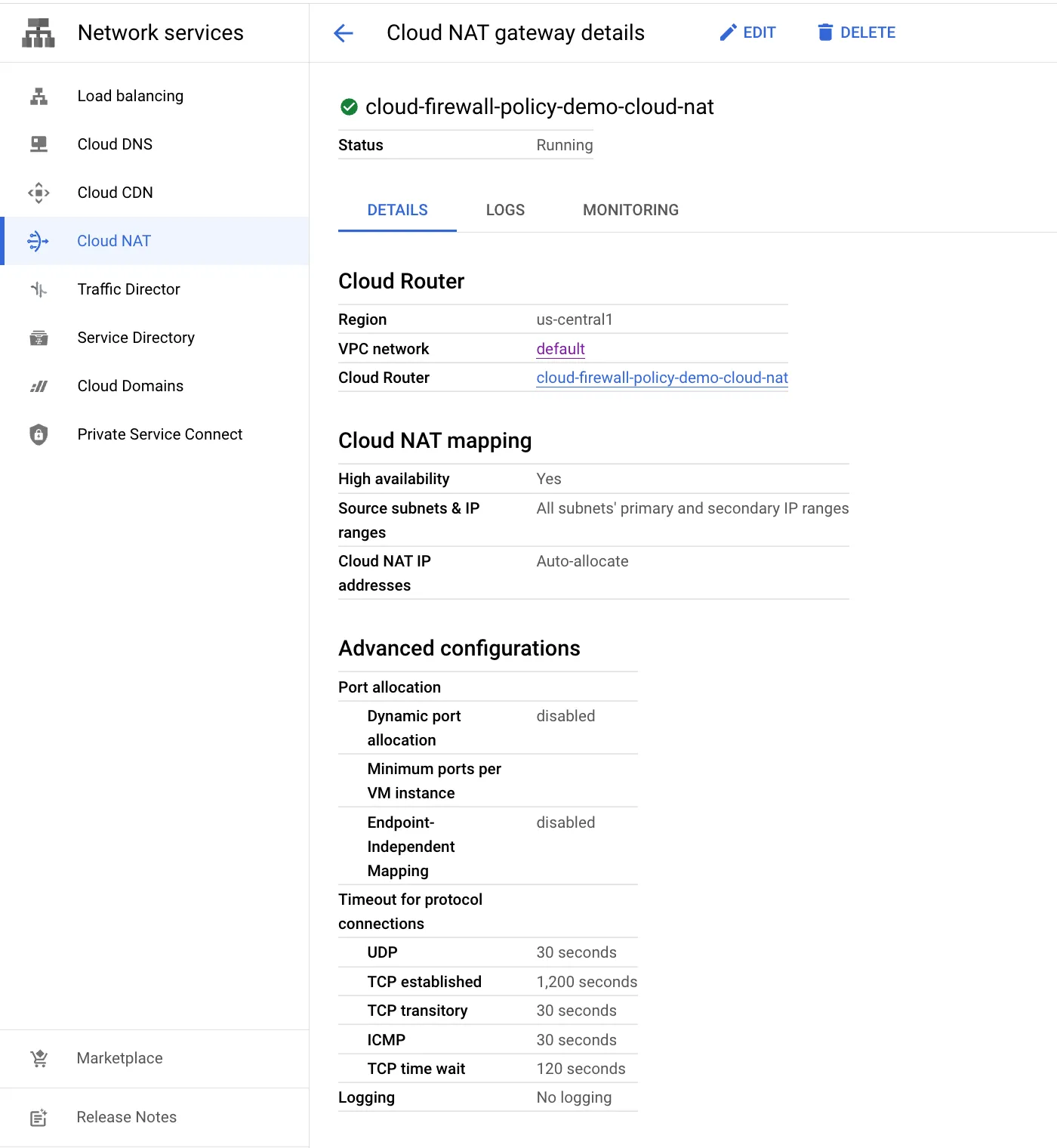
Create a Cloud router in the required region.
gcloud compute routers create cloud-firewall-policy-demo-cloud-nat \
--network=$NETWORK_NAME \
--region=$REGION
Create the Cloud NAT gateway.
gcloud compute routers nats create cloud-firewall-policy-demo-cloud-nat \ --router=cloud-firewall-policy-demo-cloud-nat \ --region=$REGION \ --auto-allocate-nat-external-ips \ --nat-all-subnet-ip-ranges
Setup firewall policy rules
Firewall policies come in three flavours.
- Hierarchical firewall policies let you create and enforce a consistent firewall policy across your organization. You can assign hierarchical firewall policies to the organization as a whole or individual folders.
- Global network firewall policies enable you to batch update all firewall rules by grouping them into a single policy object, and the rules apply to all regions.
- Regional network firewall policies let you create and enforce a consistent firewall policy across all subnetworks within a region in your VPC network.
Create a Global Network firewall policy for this setup.
gcloud compute network-firewall-policies create global-demo-firewall-policy \ --global
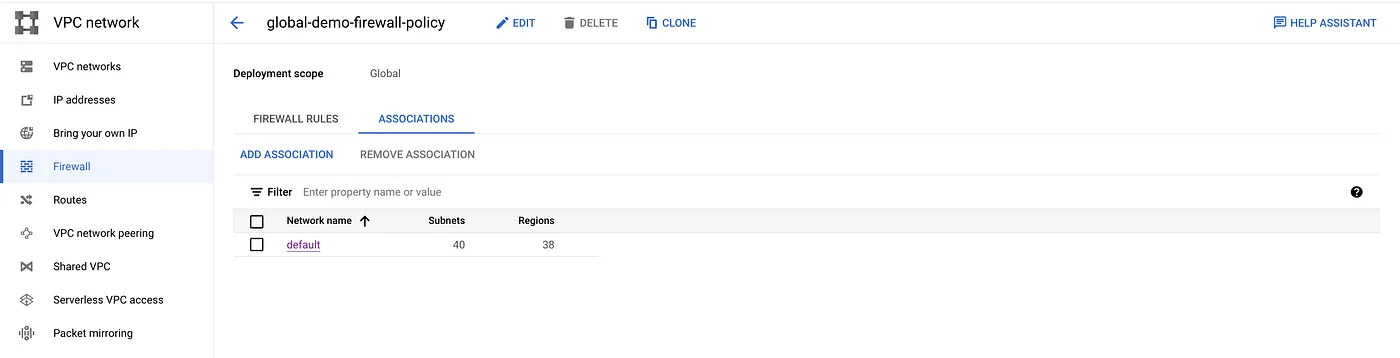
Create a new association between the firewall policy and the target network.
gcloud compute network-firewall-policies associations create \ --firewall-policy=global-demo-firewall-policy \ --network=$NETWORK_NAME --global-firewall-policy
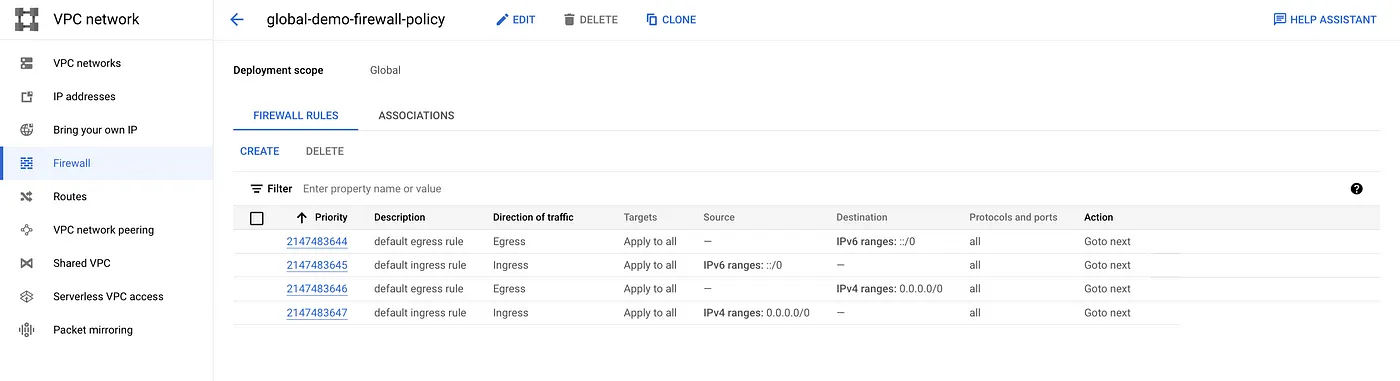
Default firewall rules are part of the policy
Network association to the policy
We now have all the required resources created to enforce FQDN egress filtering using the FQDN objects in firewall policy rules. The next step is to add the necessary rules to the firewall policy.
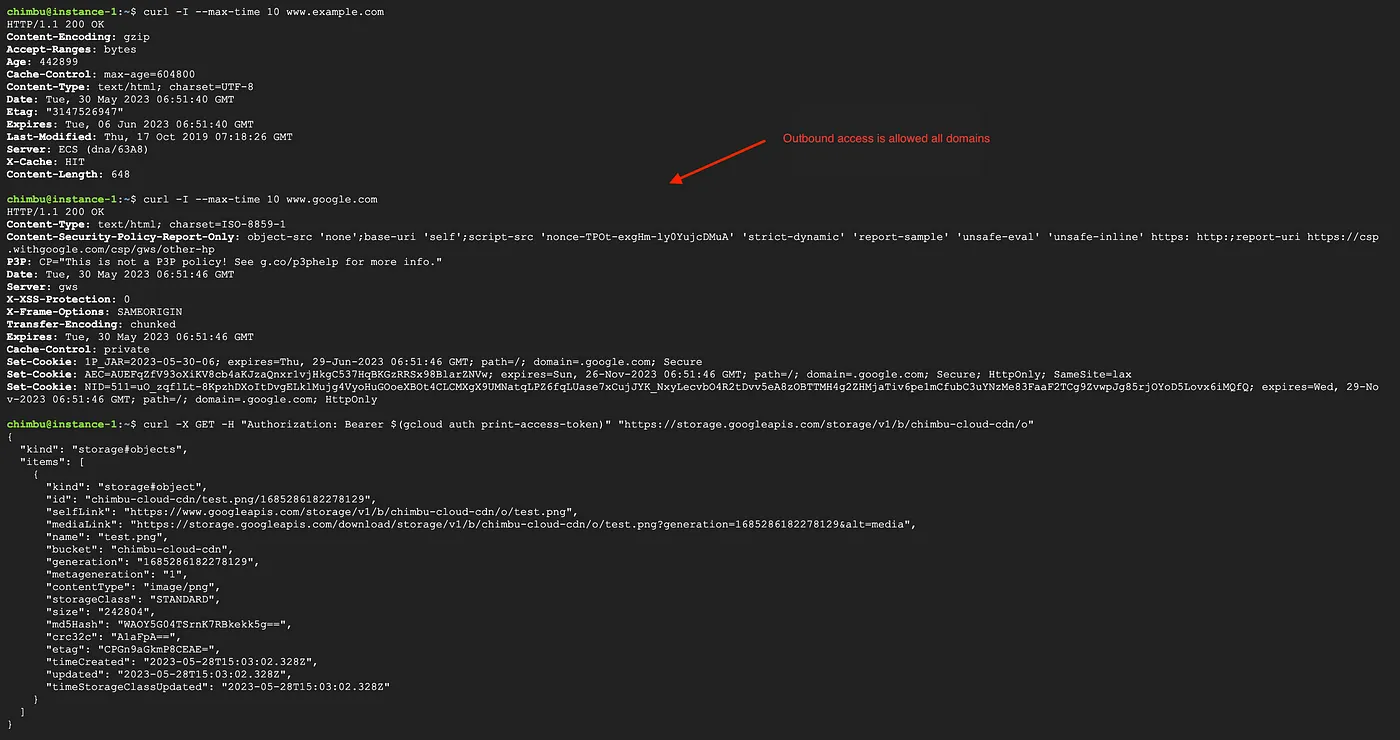
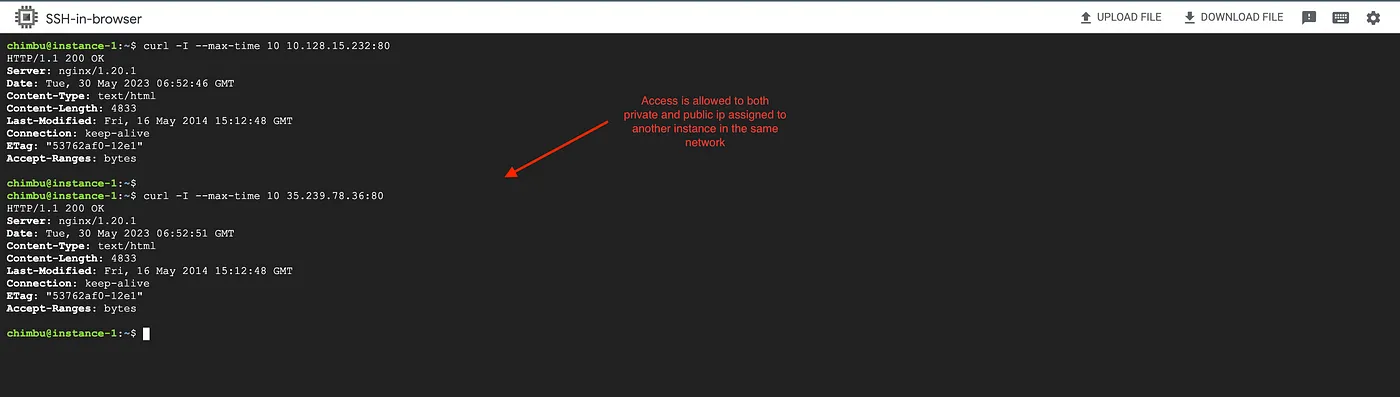
No restrictions are currently applied to egress traffic, and instances in the network have unrestricted internet access.
For this setup, we will allow outbound traffic only to www.example.com, the public IP address assigned to private.googleapis.com and block other internet traffic.
Create a Default ingress allow rule, and Inbound access is permitted without restriction, but customize the rule based on your requirement.
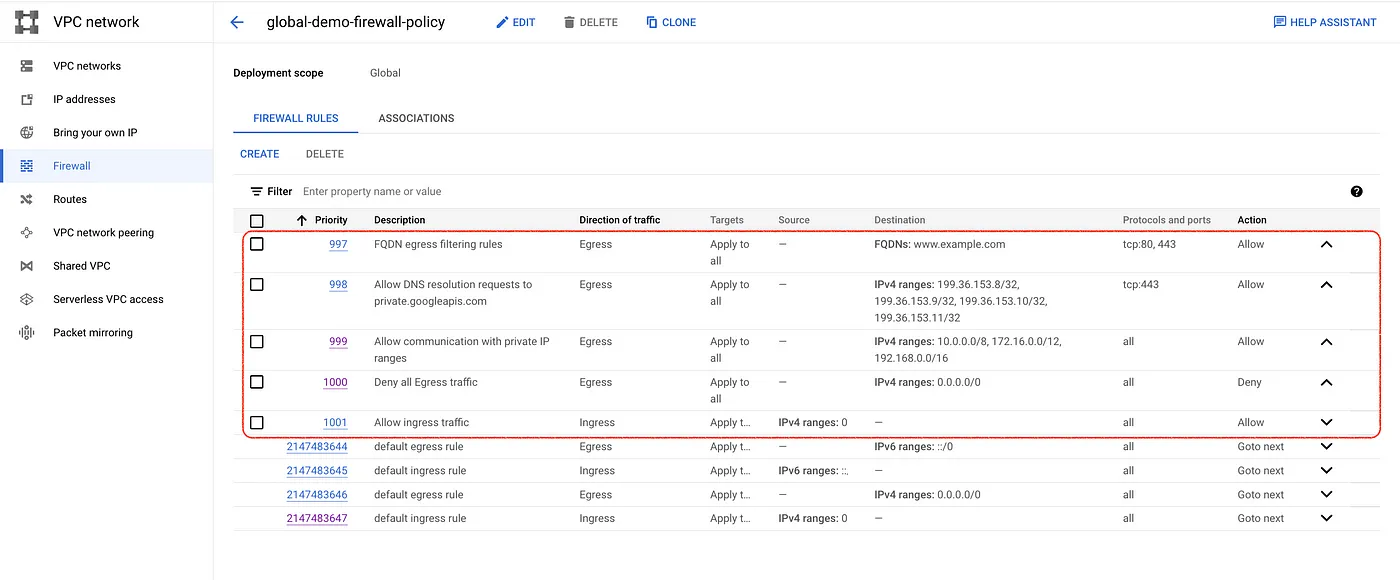
gcloud compute network-firewall-policies rules create 1001 \ --firewall-policy="global-demo-firewall-policy" \ --action="allow" \ --direction="INGRESS" \ --description="Allow ingress traffic" \ --src-ip-ranges="0.0.0.0/0" \ --layer4-configs="all" \ --global-firewall-policy
Create a firewall rule to allow communication with private IP ranges. Ensure the rule allows any other custom private ranges used in your environment to ensure communication between instances are not affected.
gcloud compute network-firewall-policies rules create 999 \ --firewall-policy="global-demo-firewall-policy" -\ -action="allow" \ --direction="EGRESS" \ --description="Allow communication with private IP ranges" \ --dest-ip-ranges="10.0.0.0/8,172.16.0.0/12,192.168.0.0/16" \ --layer4-configs="all" \ --global-firewall-policy
Create a firewall policy rule to allow outbound requests to private.googleapis.com public IPs, and these IPs are routable only within Google Cloud .
gcloud compute network-firewall-policies rules create 998 \ --firewall-policy="global-demo-firewall-policy" \ --action="allow" \ --direction="EGRESS" \ --description="Allow DNS resolution requests to private.googleapis.com" \ --dest-ip-ranges="199.36.153.8/32,199.36.153.9/32,199.36.153.10/32,199.36.153.11/32" \ --layer4-configs="tcp:443" \ --global-firewall-policy
Create a firewall policy rule to allow outbound requests to www.example.com.
gcloud compute network-firewall-policies rules create 997 \ --firewall-policy="global-demo-firewall-policy" \ --action="allow" \ --direction="EGRESS" \ --description="FQDN egress filtering rules" \ --dest-fqdns="www.example.com" \ --layer4-configs="tcp:80,tcp:443" \ --global-firewall-policy
Create a Default egress deny rule and ensure you have created allow rules for the required domains and IP ranges before creating the Deny rule.
gcloud compute network-firewall-policies rules create 1000 \ --firewall-policy="global-demo-firewall-policy" \ --action="deny" \ --direction="EGRESS" \ --description="Deny all Egress traffic" \ --dest-ip-ranges="0.0.0.0/0" \ --layer4-configs="all" \ --global-firewall-policy
Consolidated Firewall policy rules list.
The rules may take up to 30 seconds to take effect and test the network connectivity from the GCE instance or GKE pods. The outbound requests are allowed only to the domains and IP ranges in the firewall policy rules.
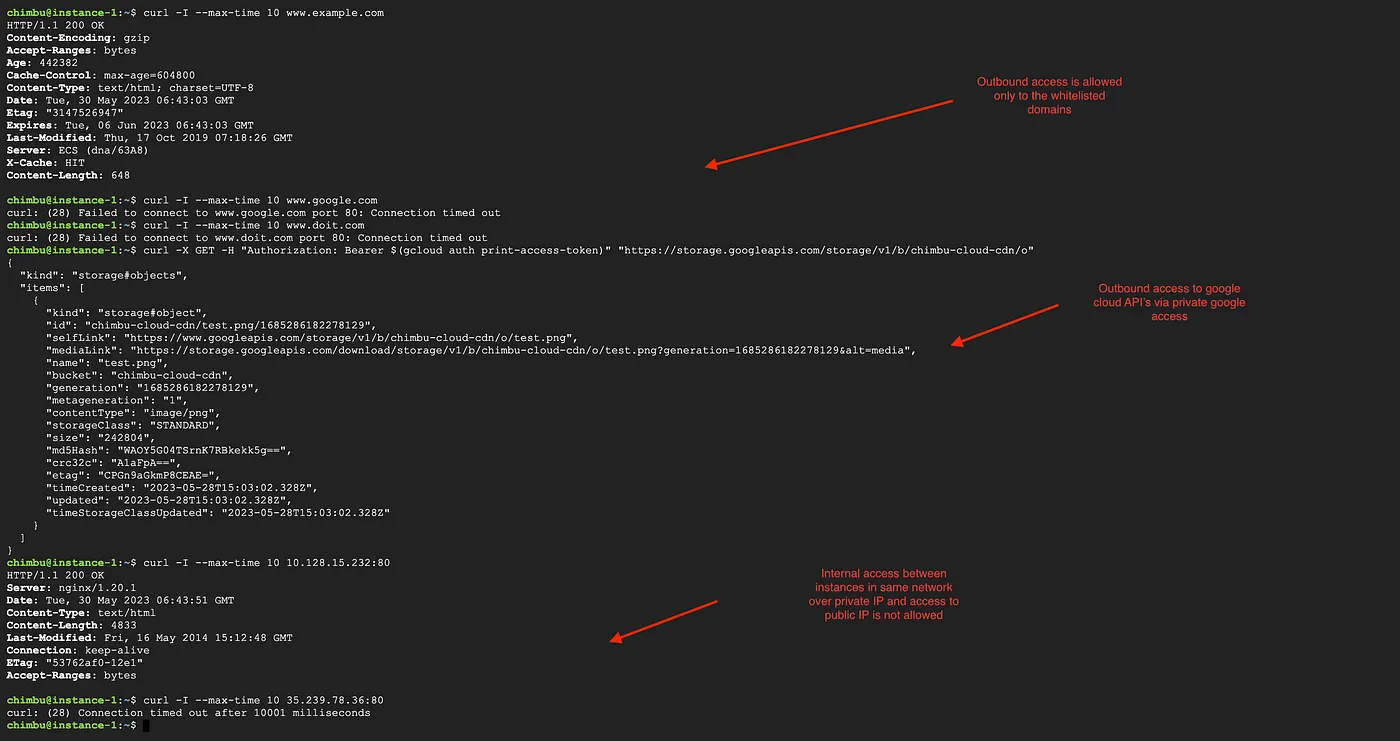
Test results after the enforcement of the firewall policy rules
Conclusion
In this example, we demonstrated how FQDN objects can be utilized in Firewall policy rules for egress filtering. This method is extremely beneficial in enhancing network security and controlling egress points.
For further information on Firewall Policy, please refer to the product page.